- Getting started
- System components and configuration
- BlackBerry AtHoc account requirements
- Install BlackBerry AtHoc
- Upgrade BlackBerry AtHoc
- Post-installation or upgrade configuration
- Set anti-virus file exclusions for database log and tempDB files
- IIS post-installation checklist
- Application pool configuration tables
- Table 1: Application pool configuration
- Table 2: Application Pool - Web Application associations for the IWS web site - enterprise configuration
- Table 3: Application Pools - Web application association for IWS Web site - standard configuration for MAS
- Table 4: IWS Services application pool configuration
- Table 5: Application pools - web application association for IWS services web site
- IIS handler mappings
- Verification checklist
- Application pool configuration tables
- Configure role-based permissions for the AtHoc Mobile App
- Uninstall ImageMagick
- (Optional) Enable message termination
- (Optional) Enable and enforce the TLS 1.2 protocol
- (Optional) Configure client certificates on the application server
- (Optional) Set the SSL client certificate
- (Optional) Install a MIR3 certificate
- (Optional) Configure new access card formats for operator auto-login
- (Optional) Update the application server registry for smart card login
- (Optional) Enable FIPS on each application server
- (Optional) Archive and MAS export service account requirements
- (Optional) Server proxy configuration
- (Optional) Restore the XML files for duplicated devices
- (Optional) Set up error pages for Self Service throttling
- Advanced server configuration
- IIS 8.5 Security Technology Implementation Guide
- Server STIG
- IISW-SV-000103: Enable log file and Event Tracing windows
- IISW-SV-000107: Sufficient web server log records for location of web server events
- IISW-SV-000108: Sufficient web server log records for source of web server events
- IISW-SV-000110: Sufficient web server log records to establish the outcome of web server events
- IISW-SV-000111: Sufficient web server log records to establish identity
- IISW-SV-000112: Web server must use Event Tracing for Windows logging option
- IISW-SV-000120: Samples, examples, and tutuorials must be removed from production server
- IISW-SV-000124: Web server must have MIMEs that invoke OS shell programs disabled
- IISW-SV-000146: Web server must not impede ability to write log record content to an audit log
- IISW-SV-000153: Web server must maintain the confidentiality of controlled information during transmission
- IISW-SV-000154: Web server must maintain the confidentiality of controlled information during transmission
- Application STIG
- IISW-SI-000206: Enable log file and Event Tracing windows
- IISW-SI-000209: Sufficient website log records to establish identity
- IISW-SI-000210: Sufficient website log records to establish identity
- IISW-SI-000211: Website must use Event Tracing for Windows logging option
- IISW-SI-000214: Website must have MIMEs that invoke OS shell programs disabled
- IISW-SI-000228: Non-ASCII characters in URLs must be prohibited
- Server STIG
- Verify BlackBerry AtHoc is operational
- Appendix A: Troubleshooting
- Appendix B: Organization duplicator object management
- BlackBerry AtHoc customer portal
- Legal notices
- BlackBerry Docs
- BlackBerry AtHoc
- BlackBerry AtHoc 7.6
- Installation and Configuration Guide
- Post-installation or upgrade configuration
- (Optional) Configure client certificates on the application server
(Optional) Configure client certificates on the application server
These steps are required if client certificates are intended to be used with the BlackBerry AtHoc system.
Configure Client Certificates on each application server so that they can make secure outbound requests to the database server.
To install and configure the client certificate, complete the following steps.
These steps assume that you already have a certificate with a private key.
- Log in to the application server.
- Copy the client certificate to the file system.
- Open Microsoft Management Console (MMC).
- From the Start menu, find MMC.
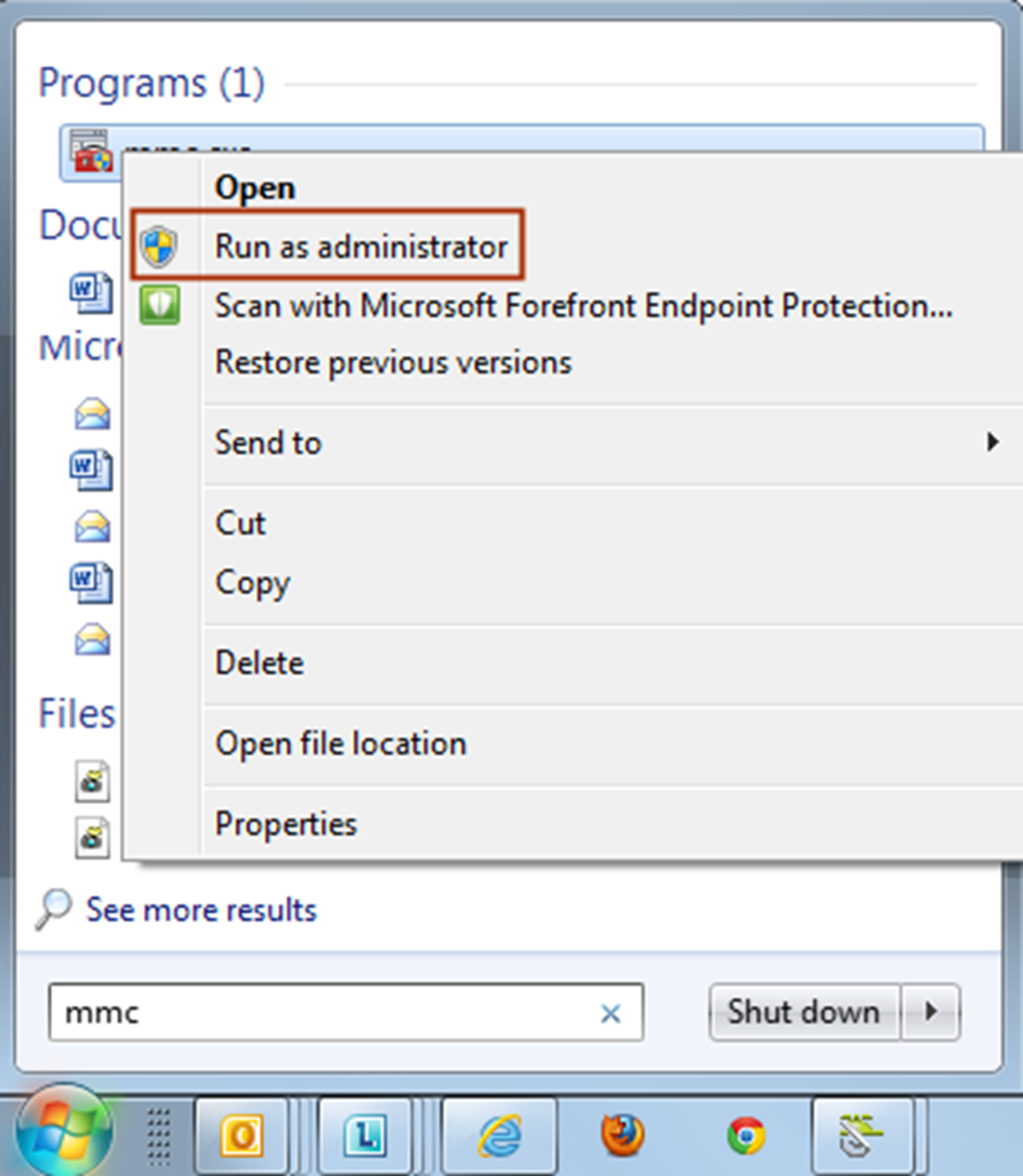
- Right click and selectRun as administrator. The console opens.The console opens.
- Add the certificate snap-in.
- ClickFileand clickAdd/Remove Snap-in...
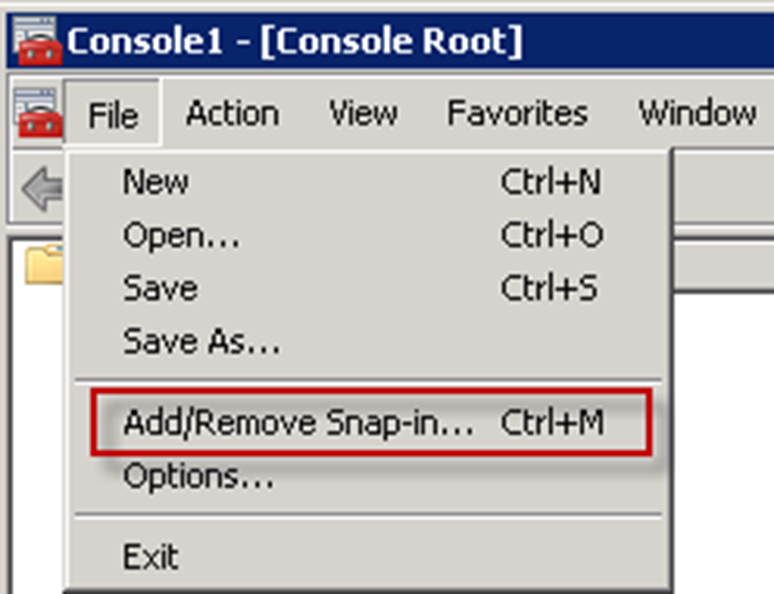
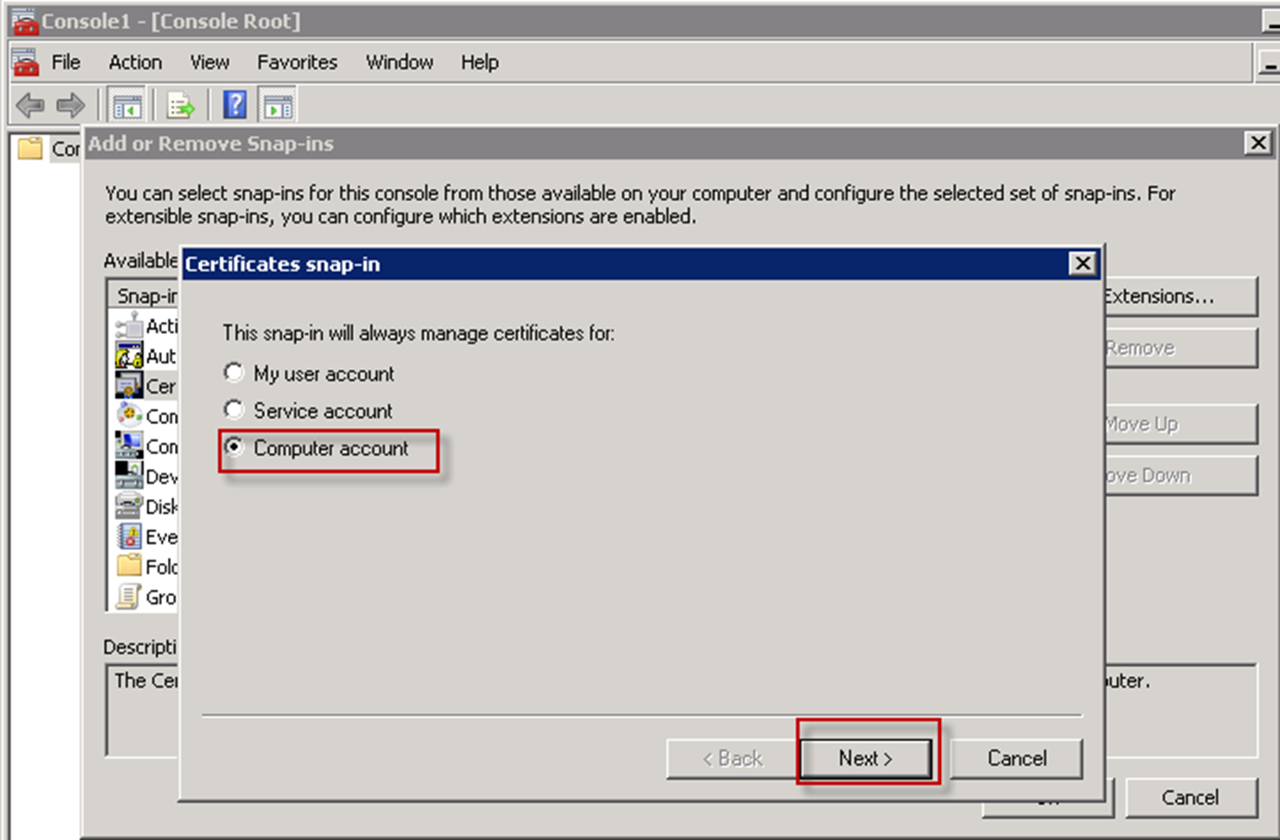
- ClickCertificatesand clickAdd.
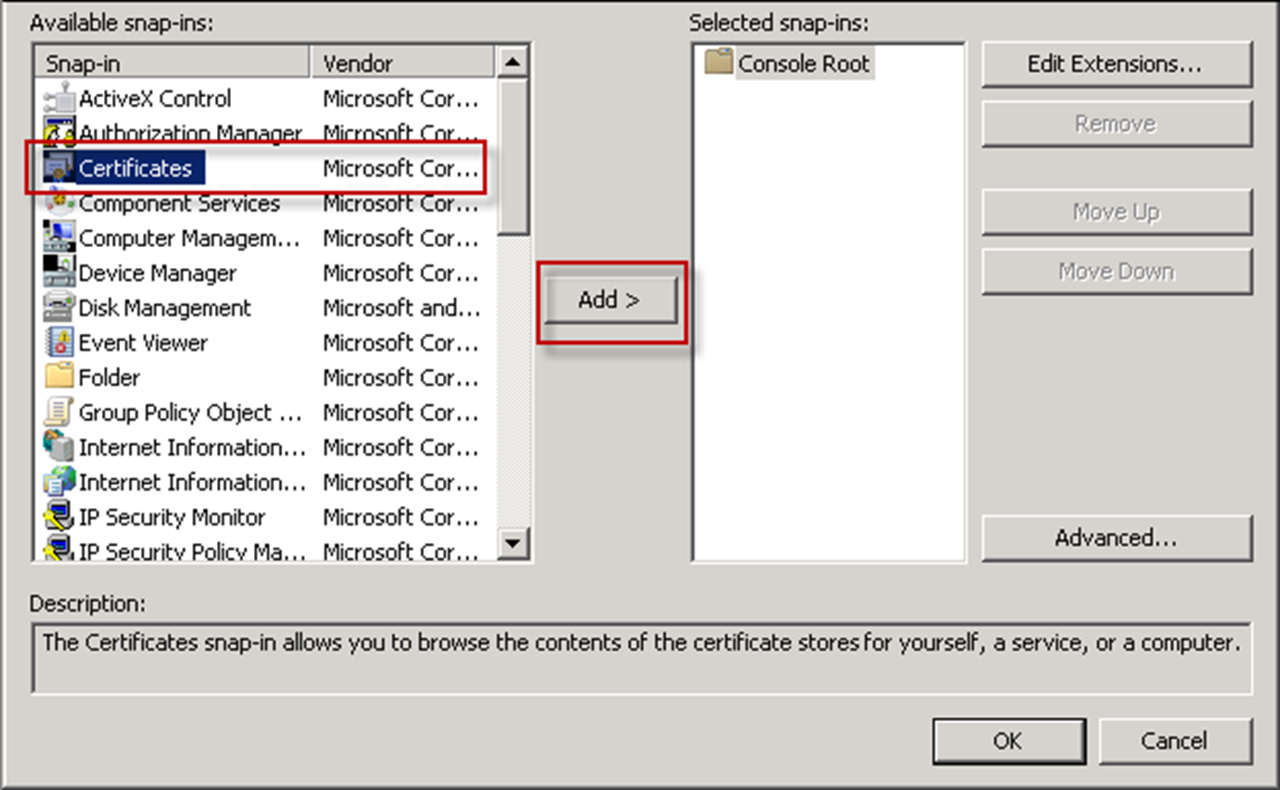 The Certificate snap-ins dialog opens.
The Certificate snap-ins dialog opens. - SelectComputer accountand clickNext.
- SelectLocal Computer.
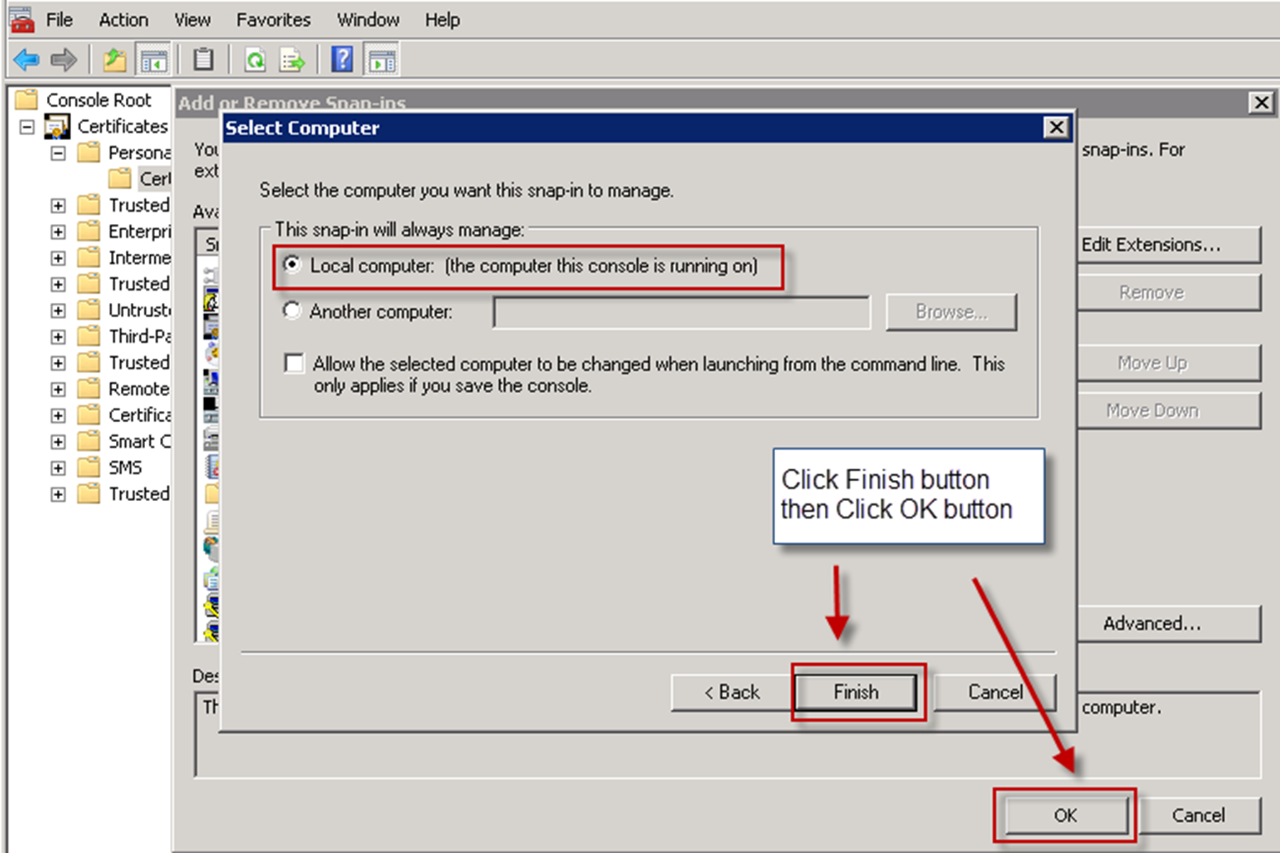
- ClickFinishand clickOK.
- Import the client certificate.
- Copy the certificate file to the application server.
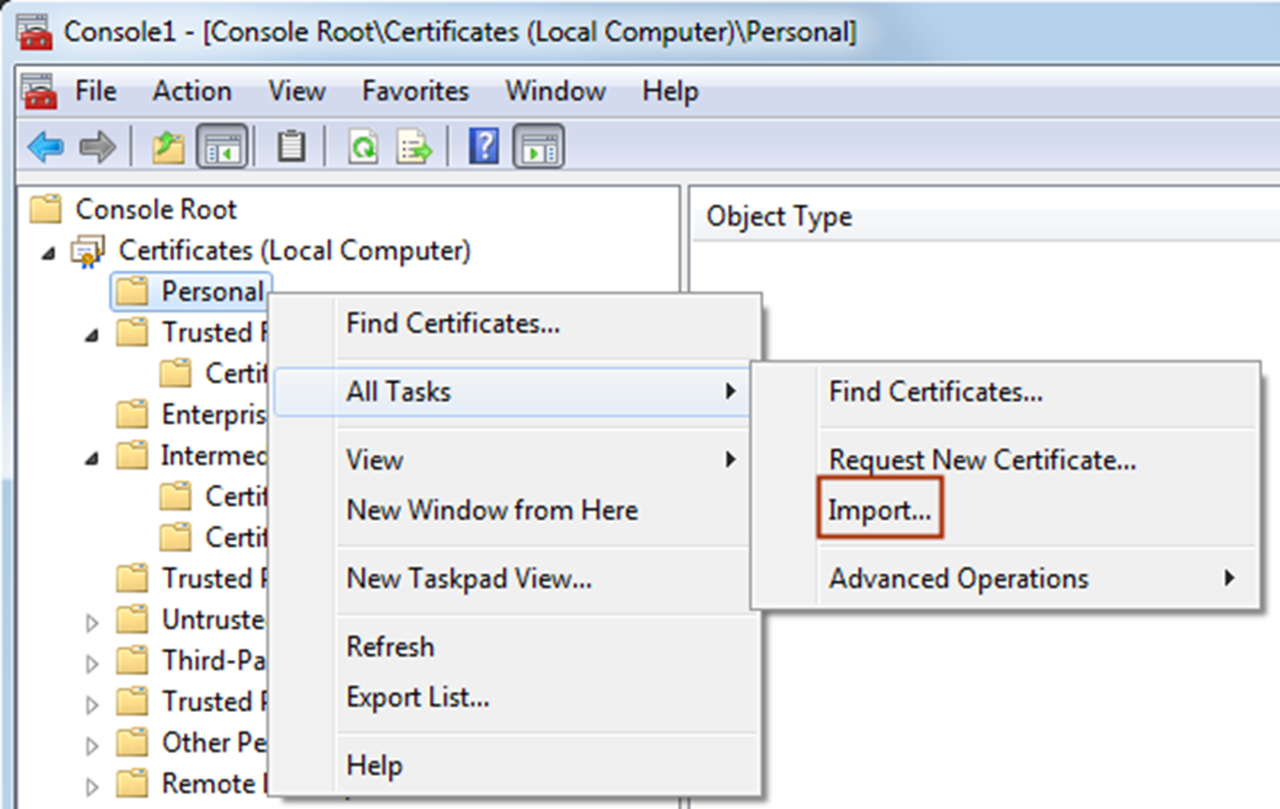
- Open MMC and navigate toCertificates>Personal.
- Right-clickPersonaland selectImport.
- Complete the import wizard.Wizard notes
- The certificate that you import must be have a private key and be of the file type .PFX or .P12.
- Store the certificate in the Personal store.
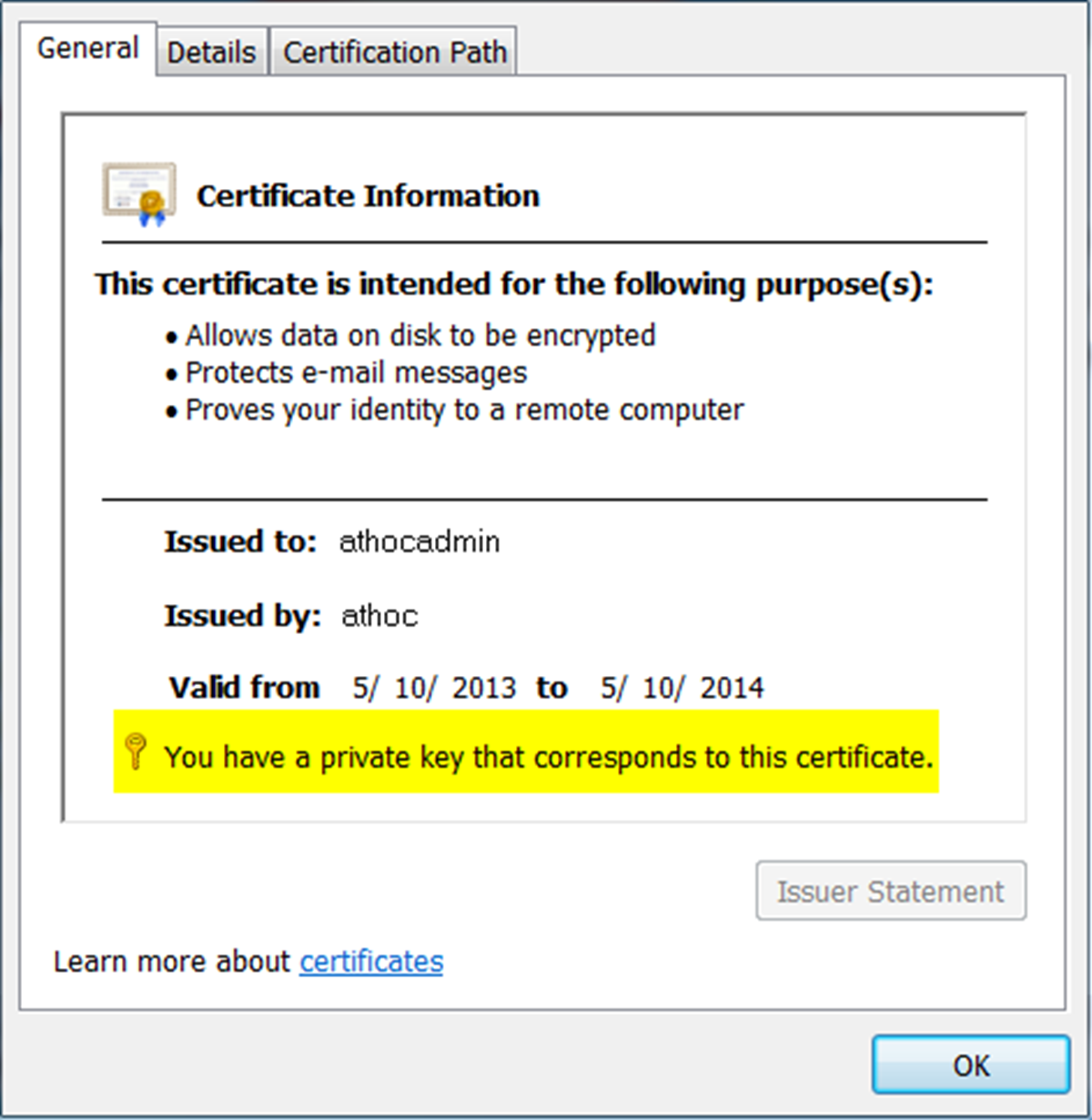
- Verify that the client certificate has a private key by opening the certificate. On theGeneraltab, look for a note following theValid fromfield.
- Repeat this process for each application server.
When you configure the IWS Services application pool accounts, ensure that the account has access to the client certificate.
When you configure IIS, ensure that the web service has access to the client certificate.